At What Layer of the Osi Model Would a Tcp or Udp Header Be Added to a Payload

This article explains the Open Systems Interconnection (OSI) model and the 7 layers of networking, in plain English.
The OSI model is a conceptual framework that is used to depict how a network functions. In manifestly English, the OSI model helped standardize the mode computer systems send data to each other.
Learning networking is a bit similar learning a language - there are lots of standards and and so some exceptions. Therefore, it'south important to really understand that the OSI model is not a set of rules. It is a tool for understanding how networks function.
Once you learn the OSI model, you will be able to further understand and appreciate this glorious entity we call the Net, as well as exist able to troubleshoot networking issues with greater fluency and ease.
All hail the Cyberspace!
Prerequisites
You don't need any prior programming or networking experience to understand this commodity. Still, y'all will need:
- Basic familiarity with common networking terms (explained below)
- A curiosity about how things work :)
Learning Objectives
Over the course of this article, you lot volition larn:
- What the OSI model is
- The purpose of each of the 7 layers
- The problems that tin happen at each of the 7 layers
- The difference between TCP/IP model and the OSI model
Common Networking Terms
Here are some mutual networking terms that you should be familiar with to become the most out of this article. I'll use these terms when I talk about OSI layers adjacent.
Nodes
A node is a physical electronic device hooked upwards to a network, for example a computer, printer, router, and so on. If prepare upwards properly, a node is capable of sending and/or receiving data over a network.
Nodes may be fix side by side to i other, wherein Node A can connect directly to Node B, or in that location may be an intermediate node, like a switch or a router, prepare between Node A and Node B.
Typically, routers connect networks to the Internet and switches operate within a network to facilitate intra-network communication. Learn more than about hub vs. switch vs. router.
Hither's an case:
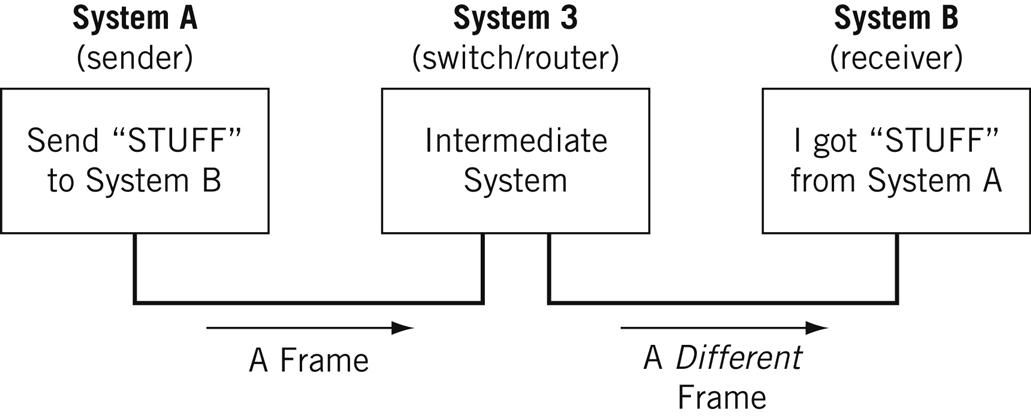
For the nitpicky among usa (yeah, I run across yous), host is another term that y'all will run into in networking. I will define a host as a type of node that requires an IP accost. All hosts are nodes, just not all nodes are hosts. Please Tweet angrily at me if you disagree.
Links
Links connect nodes on a network. Links can be wired, like Ethernet, or cable-free, like WiFi.
Links to can either be point-to-point, where Node A is connected to Node B, or multipoint, where Node A is connected to Node B and Node C.
When we're talking about information being transmitted, this may also be described as a one-to-one vs. a ane-to-many relationship.
Protocol
A protocol is a mutually agreed upon set of rules that allows two nodes on a network to exchange information.
"A protocol defines the rules governing the syntax (what tin be communicated), semantics (how it can be communicated), and synchronization (when and at what speed it can exist communicated) of the communications procedure. Protocols can be implemented on hardware, software, or a combination of both. Protocols can be created by anyone, but the most widely adopted protocols are based on standards." - The Illustrated Network.
Both wired and cable-free links tin can have protocols.
While anyone can create a protocol, the most widely adopted protocols are often based on standards published by Internet organizations such as the Cyberspace Engineering Task Force (IETF).
Networks
A network is a general term for a group of computers, printers, or whatever other device that wants to share data.
Network types include LAN, HAN, CAN, Homo, WAN, BAN, or VPN. Recollect I'thousand just randomly rhyming things with the discussion can? I tin can't say I am - these are all real network types. Learn more here.
Topology
Topology describes how nodes and links fit together in a network configuration, often depicted in a diagram. Hither are some common network topology types:
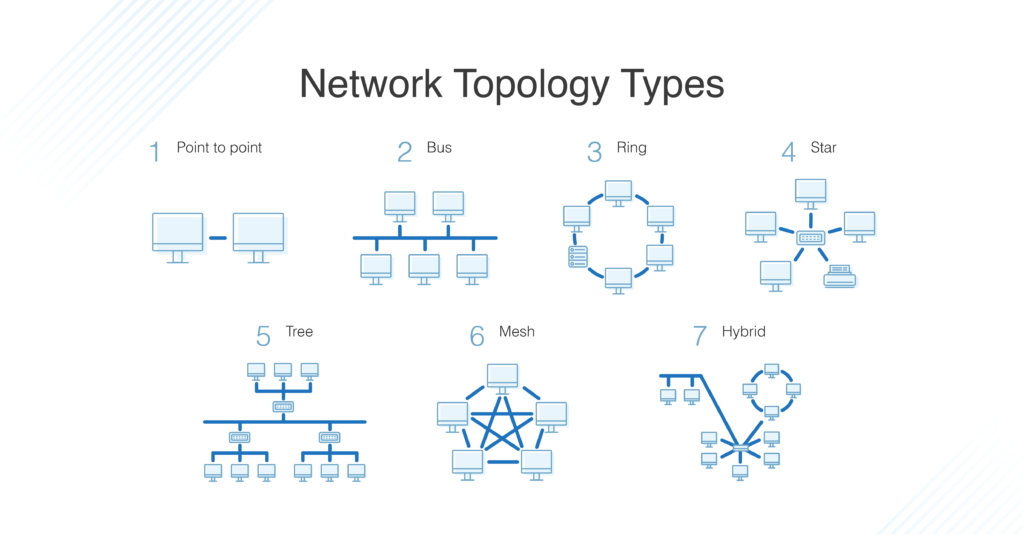
A network consists of nodes, links between nodes, and protocols that govern data manual betwixt nodes.
At whatsoever scale and complexity networks get to, you will empathise what's happening in all computer networks by learning the OSI model and vii layers of networking.
What is the OSI Model?
The OSI model consists of vii layers of networking.
Offset, what's a layer?

Ooo, lair.
No, a layer - not a lair. Here there are no dragons.
A layer is a manner of categorizing and grouping functionality and behavior on and of a network.
In the OSI model, layers are organized from the nigh tangible and nearly concrete, to less tangible and less physical simply closer to the terminate user.
Each layer abstracts lower level functionality away until by the fourth dimension you lot get to the highest layer. All the details and inner workings of all the other layers are hidden from the end user.
How to remember all the names of the layers? Piece of cake.
- Please | Physical Layer
- Do | Information Link Layer
- Not | Network Layer
- Tell (the) | Send Layer
- Undercover | Session Layer
- Password (to) | Presentation Layer
- Anyone | Application Layer
Keep in mind that while certain technologies, like protocols, may logically "belong to" one layer more than another, not all technologies fit neatly into a single layer in the OSI model. For case, Ethernet, 802.eleven (Wifi) and the Address Resolution Protocol (ARP) procedure operate on >i layer.
The OSI is a model and a tool, not a set of rules.
OSI Layer 1
Layer 1 is the physical layer. There's a lot of technology in Layer i - everything from physical network devices, cabling, to how the cables claw up to the devices. Plus if we don't need cables, what the signal type and transmission methods are (for instance, wireless broadband).
Instead of listing every type of technology in Layer i, I've created broader categories for these technologies. I encourage readers to larn more about each of these categories:
- Nodes (devices) and networking hardware components. Devices include hubs, repeaters, routers, computers, printers, and and so on. Hardware components that alive within of these devices include antennas, amplifiers, Network Interface Cards (NICs), and more than.
- Device interface mechanics. How and where does a cable connect to a device (cable connector and device socket)? What is the size and shape of the connector, and how many pins does it have? What dictates when a pivot is active or inactive?
- Functional and procedural logic. What is the function of each pin in the connector - send or receive? What procedural logic dictates the sequence of events so a node can beginning to communicate with some other node on Layer two?
- Cabling protocols and specifications. Ethernet (True cat), USB, Digital Subscriber Line (DSL), and more. Specifications include maximum cable length, modulation techniques, radio specifications, line coding, and $.25 synchronization (more on that below).
- Cable types. Options include shielded or unshielded twisted pair, untwisted pair, coaxial so on. Learn more most cable types hither.
- Signal blazon. Baseband is a single chip stream at a fourth dimension, like a railway track - one-manner only. Broadband consists of multiple bit streams at the same fourth dimension, like a bi-directional highway.
- Signal transmission method (may be wired or cable-free). Options include electric (Ethernet), light (optical networks, fiber optics), radio waves (802.xi WiFi, a/b/g/northward/ac/ax variants or Bluetooth). If cablevision-gratuitous, then besides consider frequency: 2.5 GHz vs. v GHz. If it's cabled, consider voltage. If cabled and Ethernet, as well consider networking standards like 100BASE-T and related standards.
The data unit of measurement on Layer 1 is the scrap.
A bit the smallest unit of transmittable digital information. Bits are binary, so either a 0 or a ane. Bytes, consisting of eight bits, are used to represent single characters, similar a letter of the alphabet, numeral, or symbol.
Bits are sent to and from hardware devices in accordance with the supported data rate (manual rate, in number of $.25 per second or millisecond) and are synchronized so the number of bits sent and received per unit of time remains consistent (this is chosen flake synchronization). The manner bits are transmitted depends on the signal transmission method.
Nodes can transport, receive, or transport and receive bits. If they tin only exercise one, then the node uses a simplex mode. If they can do both, and so the node uses a duplex way. If a node can transport and receive at the same time, it's total-duplex – if non, information technology'south but half-duplex.
The original Ethernet was half-duplex. Full-duplex Ethernet is an option at present, given the correct equipment.
How to Troubleshoot OSI Layer ane Issues
Hither are some Layer one bug to watch out for:
- Defunct cables, for example damaged wires or broken connectors
- Broken hardware network devices, for case damaged circuits
- Stuff being unplugged (...we've all been there)
If at that place are bug in Layer ane, annihilation beyond Layer 1 will non function properly.
TL;DR
Layer 1 contains the infrastructure that makes advice on networks possible.
Information technology defines the electric, mechanical, procedural, and functional specifications for activating, maintaining, and deactivating physical links between network devices. - Source
Fun fact: deep-sea communications cables transmit data around the world. This map volition blow your mind: https://world wide web.submarinecablemap.com/
And because you made it this far, here's a koala:

OSI Layer 2
Layer 2 is the data link layer. Layer ii defines how data is formatted for manual, how much data tin catamenia between nodes, for how long, and what to practise when errors are detected in this menstruum.
In more official tech terms:
- Line subject area. Who should talk for how long? How long should nodes be able to transit information for?
- Menses command. How much data should exist transmitted?
- Error control - detection and correction. All data transmission methods accept potential for errors, from electrical spikes to dingy connectors. Once Layer 2 technologies tell network administrators almost an consequence on Layer two or Layer ane, the system ambassador can correct for those errors on subsequent layers. Layer ii is more often than not concerned with mistake detection, not error correction. (Source)
At that place are two distinct sublayers within Layer ii:
- Media Access Control (MAC): the MAC sublayer handles the assignment of a hardware identification number, chosen a MAC address, that uniquely identifies each device on a network. No two devices should have the aforementioned MAC address. The MAC address is assigned at the indicate of manufacturing. It is automatically recognized past most networks. MAC addresses live on Network Interface Cards (NICs). Switches go along track of all MAC addresses on a network. Acquire more about MAC addresses on PC Mag and in this article. Learn more about network switches hither.
- Logical Link Control (LLC): the LLC sublayer handles framing addressing and flow control. The speed depends on the link between nodes, for example Ethernet or Wifi.
The information unit on Layer 2 is a frame.
Each frame contains a frame header, trunk, and a frame trailer:
- Header: typically includes MAC addresses for the source and destination nodes.
- Body: consists of the $.25 being transmitted.
- Trailer: includes error detection information. When errors are detected, and depending on the implementation or configuration of a network or protocol, frames may be discarded or the error may be reported up to higher layers for farther error correction. Examples of error detection mechanisms: Cyclic Redundancy Check (CRC) and Frame Check Sequence (FCS). Learn more virtually error detection techniques here.
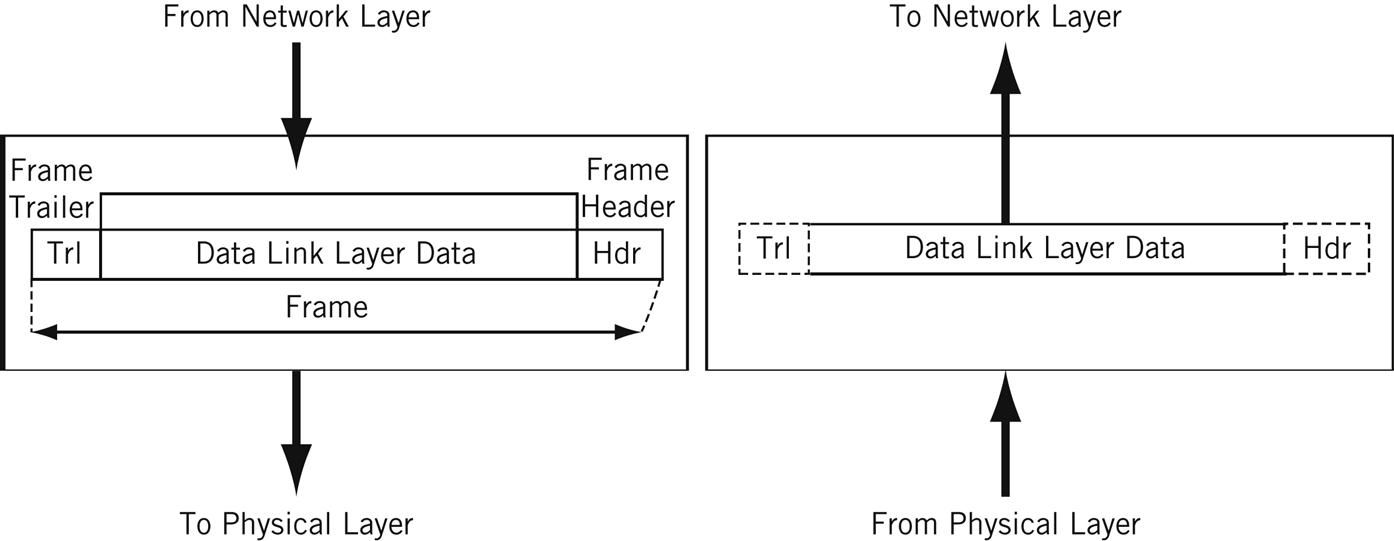
Typically there is a maximum frame size limit, called an Maximum Transmission Unit of measurement, MTU. Colossal frames exceed the standard MTU, acquire more well-nigh jumbo frames hither.
How to Troubleshoot OSI Layer 2 Problems
Here are some Layer ii issues to watch out for:
- All the problems that tin can occur on Layer 1
- Unsuccessful connections (sessions) between two nodes
- Sessions that are successfully established just intermittently fail
- Frame collisions
TL;DR
The Information Link Layer allows nodes to communicate with each other within a local area network. The foundations of line discipline, flow command, and mistake control are established in this layer.
OSI Layer 3
Layer 3 is the network layer. This is where we transport data between and beyond networks through the use of routers. Instead of but node-to-node communication, we tin can now do network-to-network communication.
Routers are the workhorse of Layer 3 - we couldn't take Layer 3 without them. They move data packets beyond multiple networks.
Not only do they connect to Net Service Providers (ISPs) to provide admission to the Internet, they also go on rails of what'south on its network (remember that switches continue track of all MAC addresses on a network), what other networks it'due south connected to, and the different paths for routing information packets beyond these networks.
Routers store all of this addressing and routing information in routing tables.
Here's a uncomplicated example of a routing table:
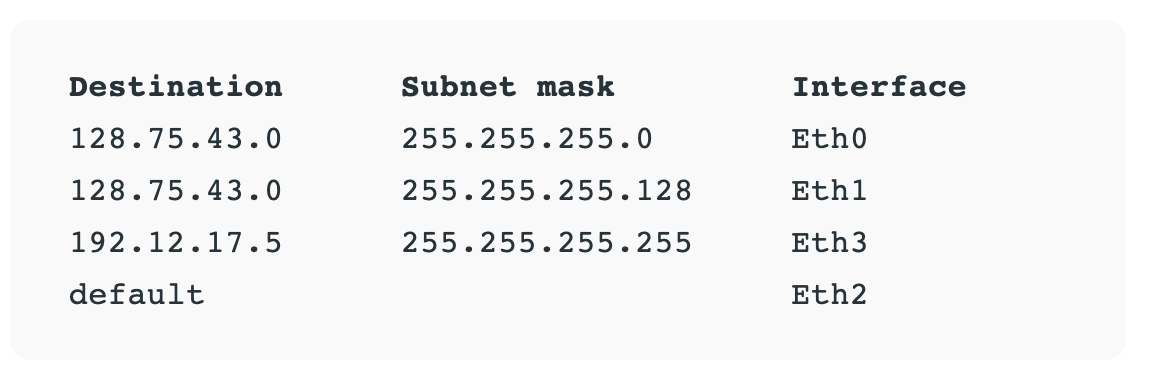
The information unit on Layer iii is the data packet. Typically, each data packet contains a frame plus an IP address information wrapper. In other words, frames are encapsulated by Layer 3 addressing information.
The data being transmitted in a packet is too sometimes called the payload. While each packet has everything information technology needs to become to its destination, whether or non it makes it there is another story.
Layer three transmissions are connectionless, or all-time effort - they don't practice anything merely send the traffic where information technology's supposed to go. More on information transport protocols on Layer 4.
Once a node is continued to the Internet, it is assigned an Cyberspace Protocol (IP) address, which looks either like 172.16. 254.one (IPv4 address convention) or like 2001:0db8:85a3:0000:0000:8a2e:0370:7334 (IPv6 address convention). Routers apply IP addresses in their routing tables.
IP addresses are associated with the physical node's MAC address via the Address Resolution Protocol (ARP), which resolves MAC addresses with the node's corresponding IP accost.
ARP is conventionally considered part of Layer ii, only since IP addresses don't exist until Layer three, information technology's likewise part of Layer 3.
How to Troubleshoot OSI Layer 3 Problems
Hither are some Layer 3 problems to watch out for:
- All the issues that can crop up on previous layers :)
- Faulty or not-functional router or other node
- IP address is incorrectly configured
Many answers to Layer 3 questions will crave the use of control-line tools like ping, trace, show ip road, or prove ip protocols. Learn more about troubleshooting on layer 1-3 here.
TL;DR
The Network Layer allows nodes to connect to the Internet and send information beyond different networks.
OSI Layer 4
Layer iv is the ship layer. This where nosotros swoop into the nitty gritty specifics of the connectedness betwixt two nodes and how information is transmitted betwixt them. It builds on the functions of Layer 2 - line subject, menstruation command, and error control.
This layer is also responsible for data parcel segmentation, or how data packets are broken upwardly and sent over the network.
Unlike the previous layer, Layer iv also has an agreement of the whole message, not just the contents of each individual data bundle. With this understanding, Layer 4 is able to manage network congestion by non sending all the packets at once.
The information units of Layer 4 go past a few names. For TCP, the data unit is a packet. For UDP, a packet is referred to as a datagram. I'll but use the term data packet here for the sake of simplicity.
Manual Control Protocol (TCP) and User Datagram Protocol (UDP) are two of the near well-known protocols in Layer 4.
TCP, a connexion-oriented protocol, prioritizes information quality over speed.
TCP explicitly establishes a connection with the destination node and requires a handshake between the source and destination nodes when data is transmitted. The handshake confirms that data was received. If the destination node does not receive all of the data, TCP will ask for a retry.
TCP also ensures that packets are delivered or reassembled in the correct club. Acquire more well-nigh TCP here.
UDP, a connectionless protocol, prioritizes speed over information quality. UDP does not require a handshake, which is why it's called connectionless.
Because UDP doesn't have to look for this acknowledgement, it can transport information at a faster rate, but non all of the data may be successfully transmitted and we'd never know.
If information is dissever up into multiple datagrams, unless those datagrams incorporate a sequence number, UDP does non ensure that packets are reassembled in the correct order. Learn more near UDP hither.
TCP and UDP both send data to specific ports on a network device, which has an IP address. The combination of the IP address and the port number is chosen a socket.
Larn more about sockets here.
Acquire more almost the differences and similarities between these two protocols here.
How to Troubleshoot OSI Layer 4 Problems
Here are some Layer 4 problems to watch out for:
- All the problems that tin ingather up on previous layers :)
- Blocked ports - check your Admission Command Lists (ACL) & firewalls
- Quality of Service (QoS) settings. QoS is a characteristic of routers/switches that can prioritize traffic, and they can really muck things up. Learn more well-nigh QoS here.
TL;DR
The Ship Layer provides end-to-cease transmission of a message by segmenting a message into multiple data packets; the layer supports connection-oriented and connectionless communication.
OSI Layer 5
Layer five is the session layer. This layer establishes, maintains, and terminates sessions.
A session is a mutually agreed upon connection that is established betwixt two network applications. Non 2 nodes! Nope, we've moved on from nodes. They were so Layer 4.
Just kidding, we even so have nodes, but Layer 5 doesn't need to retain the concept of a node because that's been bathetic out (taken care of) by previous layers.
And so a session is a connexion that is established between two specific end-user applications. In that location are two important concepts to consider here:
- Client and server model: the application requesting the information is called the customer, and the application that has the requested information is chosen the server.
- Request and response model: while a session is being established and during a session, there is a abiding dorsum-and-forth of requests for data and responses containing that data or "hey, I don't have what you're requesting."
Sessions may exist open up for a very curt amount of time or a long amount of fourth dimension. They may fail sometimes, too.
Depending on the protocol in question, various failure resolution processes may kicking in. Depending on the applications/protocols/hardware in utilize, sessions may support simplex, half-duplex, or full-duplex modes.
Examples of protocols on Layer 5 include Network Basic Input Output Organization (NetBIOS) and Remote Procedure Call Protocol (RPC), and many others.
From here on out (layer 5 and up), networks are focused on ways of making connections to end-user applications and displaying information to the user.
How to Troubleshoot OSI Layer 5 Issues
Here are some Layer v bug to lookout out for:
- Servers are unavailable
- Servers are incorrectly configured, for example Apache or PHP configs
- Session failure - disconnect, timeout, and then on.
TL;DR
The Session Layer initiates, maintains, and terminates connections between two end-user applications. Information technology responds to requests from the presentation layer and issues requests to the transport layer.
OSI Layer 6
Layer six is the presentation layer. This layer is responsible for data formatting, such every bit character encoding and conversions, and data encryption.
The operating system that hosts the finish-user application is typically involved in Layer half dozen processes. This functionality is non ever implemented in a network protocol.
Layer 6 makes sure that end-user applications operating on Layer vii can successfully consume information and, of course, somewhen display it.
There are iii data formatting methods to be aware of:
- American Standard Code for Information Interchange (ASCII): this 7-bit encoding technique is the almost widely used standard for character encoding. One superset is ISO-8859-1, which provides most of the characters necessary for languages spoken in Western Europe.
- Extended Binary-Coded Decimal Interchange Code (EBDCIC): designed by IBM for mainframe usage. This encoding is incompatible with other character encoding methods.
- Unicode: character encodings can exist done with 32-, 16-, or 8-flake characters and attempts to accommodate every known, written alphabet.
Acquire more well-nigh character encoding methods in this article, and also here.
Encryption: SSL or TLS encryption protocols live on Layer 6. These encryption protocols help ensure that transmitted data is less vulnerable to malicious actors by providing authentication and data encryption for nodes operating on a network. TLS is the successor to SSL.
How to Troubleshoot OSI Layer 6 Problems
Here are some Layer 6 problems to watch out for:
- Non-real or corrupted drivers
- Incorrect OS user access level
TL;DR
The Presentation Layer formats and encrypts data.
OSI Layer seven
Layer vii is the awarding layer.
True to its name, this is the layer that is ultimately responsible for supporting services used past end-user applications. Applications include software programs that are installed on the operating organisation, similar Internet browsers (for example, Firefox) or word processing programs (for example, Microsoft Word).
Applications can perform specialized network functions under the hood and crave specialized services that autumn under the umbrella of Layer 7.
Electronic mail programs, for example, are specifically created to run over a network and utilise networking functionality, such as e-mail protocols, which autumn under Layer 7.
Applications will besides control end-user interaction, such as security checks (for instance, MFA), identification of two participants, initiation of an commutation of information, and so on.
Protocols that operate on this level include File Transfer Protocol (FTP), Secure Shell (SSH), Simple Mail Transfer Protocol (SMTP), Net Message Access Protocol (IMAP), Domain Name Service (DNS), and Hypertext Transfer Protocol (HTTP).
While each of these protocols serve dissimilar functions and operate differently, on a high level they all facilitate the communication of information. (Source)
How to Troubleshoot OSI Layer 7 Issues
Here are some Layer vii issues to watch out for:
- All problems on previous layers
- Incorrectly configured software applications
- User error (... we've all been there)
TL;DR
The Application Layer owns the services and functions that stop-user applications need to piece of work. It does non include the applications themselves.
Decision
Our Layer 1 koala is all grown upwardly.

Learning cheque - can y'all apply makeup to a koala?
Don't accept a koala?
Well - answer these questions instead. Information technology's the next best thing, I promise.
- What is the OSI model?
- What are each of the layers?
- How could I employ this information to troubleshoot networking bug?
Congratulations - you've taken i step further to understanding the glorious entity nosotros call the Internet.
Learning Resources
Many, very smart people take written unabridged books about the OSI model or entire books about specific layers. I encourage readers to bank check out any O'Reilly-published books nigh the subject or about network technology in general.
Here are some resources I used when writing this article:
- The Illustrated Network, 2nd Edition
- Protocol Data Unit (PDU): https://www.geeksforgeeks.org/difference-between-segments-packets-and-frames/
- Troubleshooting Along the OSI Model: https://world wide web.pearsonitcertification.com/manufactures/article.aspx?p=1730891
- The OSI Model Demystified: https://www.youtube.com/watch?v=HEEnLZV2wGI
- OSI Model for Dummies: https://www.dummies.com/programming/networking/layers-in-the-osi-model-of-a-estimator-network/
About Me
Chloe Tucker is an artist and computer science enthusiast based in Portland, Oregon. Every bit a former educator, she'southward continuously searching for the intersection of learning and education, or technology and art. Achieve out to her on Twitter @_chloetucker and bank check out her website at chloe.dev.
Learn to code for gratis. freeCodeCamp's open source curriculum has helped more than than 40,000 people become jobs every bit developers. Go started
Source: https://www.freecodecamp.org/news/osi-model-networking-layers-explained-in-plain-english/
0 Response to "At What Layer of the Osi Model Would a Tcp or Udp Header Be Added to a Payload"
Postar um comentário